It is something to always take into consideration and not forget.
A smart VPN will avoid going to jail for you by not storing any of the data law enforcement wants in the first place.
Yeah, Mullvad was searched and they shrugged and said “well, go ahead” and could then proudly publish that the Swedish authorities could take zero info from there: https://mullvad.net/en/blog/update-the-swedish-authorities-answered-our-protocol-request
Just recently signed up for Mullvad… No CC numbers or email addresses, you just get a string of numbers and that’s all you need to connect with it anywhere. And you can pay with Monero.
It’s like the paranoid person’s dream.
Heck, if you want, you can pay with hard cash by mailing it with your payment token to their office. It’s pretty great when it comes to choice of privacy.
Wondering how these magicians measure quality of service then, since they collect no juicy data. I find this hard to believe.
Quality of service is usually only useful with aggregate data which is worthless for prosecuting an individual.
That’s not true. We used to collect client and server data both to detect issues and even if it was only in a subset of customers there is just some customer facing QoS issues you wouldn’t find unless you were collecting data, that wouldn’t be found on server side for example. Like let’s say iPhones make an update and you’re doing video streaming, maybe certain video formats would lag when streaming to the player but not on an android or vice versa.
Aggregate data doesn’t mean no client side data. It’s possible they’re collecting aggregate level client data too. They could go further and collect data on individuals that is not identifiable or useful to law enforcement in any way. I can think of a few ways to get anonymous usage data that allows you to improve your service while protecting your users. I don’t know their scheme but they clearly don’t need overly invasive forms of analytics as they have a solid service.
If your data is being collected then are you really private or anonymous? I can think of a lot you can infer simply from metrics in a client, time window of connection and a few metrics. That’s just removed.
Yes? I work in the identified healthcare data space, but work close to people in the unidentified space and even something as personal as health data can be obfuscated in such a way it’s impossible to trace back to an individual. Not to mention whatever they’re logging is surely many orders of magnitude less identifiable. They also have an entire page dedicated to answering these types of questions and concerns.
I worked directly for one of the two biggest log and search systems for big data for years and I can tell you that there is always a way to correlate data lol. And the data you don’t have you can always buy to help put the missing pieces together.
deleted by creator
I would put Mullvad and IVPN up there as the two VPNs I’d trust most to do things right, but I still agree with everything you’ve said.
I’d put proton there too
See the last points in the article: run by activists, and would rather shut down than cooperate with law enforcement.
I don’t know if proton is run by activists, but I do know they’ve cooperated with law enforcement by inserting code to log user requests when coming from a specific user. Plenty of articles about the court case, and it’s also why they did away with their no-log policy.
Also, are their logins token based or username based and connected to the protonmail account?
I think they only did the login thing with their mail service and email was never a protocol ment for privacy and email and vpn laws vary wildly. Feel free to correct me tho .
Sure here’s the correction, and why I’d never trust them with anything sensitive.
They had a no-log policy, and all mail is PGP encrypted on their servers and proton to proton is encrypted in transit and at rest (it doesn’t travel), decrypted only client-side in the browser or with proton bridge, with your account password acting as the PGP key password.
They could have designed the system so they couldn’t be forced to add that backdoor, or at least automatically notified all users when an unauthorized change was detected, or they could have shutdown, or they could have revoked their warrant canary, but instead they were caught when the court case came to light and they were caught with their pants down, and revoked their no-log policy. https://arstechnica.com/information-technology/2021/09/privacy-focused-protonmail-provided-a-users-ip-address-to-authorities/
This weekend, news broke that security/privacy-focused anonymous email service ProtonMail turned over a French climate activist’s IP address and browser fingerprint to Swiss authorities. This move seemingly ran counter to the well-known service’s policies, which as recently as last week stated that “by default, we do not keep any IP logs which can be linked to your anonymous email account.”
That’s why I asked if the proton VPN is token-based and completely disconnected from the proton email account, or if they’re the same login. If the latter, it’s trivial to request the IP address of email account [email protected]
deleted by creator
After the changes to their TOS I lost any trust I had in Proton
I’d put cryptostorm up there too
As others have said, Mullvad is pretty close to (if not at) 100% guarantee… No personal info whatsoever is required to be given when you sign up (including email address or payment information; you can use Monero if you want), so there isn’t really anything that they could give to authorities even if they wanted.
Even if they did keep logs (which im 99.9% sure they don’t), all that would show is an IP address, and from what I understand based on past precedent, that is not enough to identify a person on its own. But IANAL.
The purpose of these corporate white papers is to inform (impress) potential customers of actual issues. It demonstrates knowledge and implies that the company has the ability to leverage their product or service to meet whatever the challenge is.
I wouldn’t say boulder-sized because the meat of the article is true, but yes a bit of skepticism is always useful.
Meh, just Mullvad. Cops can raid em all they want; they just walk away empty handed
In this blog post we explain why competent service operators can avoid having to share sensitive information about you without facing severe legal consequences. The reasons laid out will also highlight why you are better off choosing a VPN service run by privacy activists who will prioritise principles before profits in difficult situations
is it me or does it read like someone used an LLM to write those sentences?
Sounds like the intro paragraph to someone’s term paper at uni.
This is usually how I intro documentation for tech projects. Its good practice for technical docs, doesn’t necessarily mean its an LLM
Yeah, that’s what I was going to say. Thank god that shit didn’t exist when I was in college, or every paper I ever wrote would have been flagged. I guess I write like a robot.
Worth noting that there is a strong correlation between neurodivergence and falsely getting flagged for using AI. Apparently AI sounds autistic, so lots of autistic kids were getting flagged for AI use even when they wrote it themselves.
But if it helps, even ChatGPT has had to admit that AI detection is inaccurate and schools shouldn’t be relying on them.
the twist is that the LLM writes like this because you trained it to do so with your term papers that it scraped
Haha same! There’s a place for us though: if you ever get into research, robotic writing tends to work out fairly well!
Thing is, I don’t even feel like I do write like a robot per-se… Maybe it’s more like I write like the average of every person who has ever written anything ever lol.
yeah, which LLMs seem to be very fond of. every ChatGPT-written article I’ve seen includes “to sum up” and similar fillers.
GPT loves alliteration, so at least there’s something to support your suspicion.
So, scrub my papers for alliteration. Thanks for the tip.
Use it sparingly and with style. More isn’t always better.
Ha! Author here - no LLM was used. It was an attempt to summarise the content and the key message, but it took some time to jam pack everything into two sentences.
Verifiably no logs without court order (I’m guessing canary pages have gone the way of the dodo now, probably boilerplate in the orders, maybe wrong according to the article, perhaps in some jurisdictions) would be awesome. Verified by external audit is about as good as we can get, so proton, tutanota, I think, others muchly appreciated. I think one of them setup their OS in volatile RAM, which is cool, but probably not legally protective.
No, I don’t expect you to go to jail for me, but due diligence minimising knowledge will bump you up my list of providers to choose.
One problem here is those that do verify, usually don’t allow torrenting ports, so, no ratios for you. Anyone know what the over/under is on lesser tier VPNs that port share vs a VPS (with all its potential, but which country?) vs Usenet? Looking to have a clue when the time comes, knowledge gratefully accepted :)
I love Mullvad and recommend them for everything other than torrenting. Once they disabled port forwarding I moved to AirVPN who seem to be pretty legit.
I’m not trying to keep my ratios up but I have a few torrents of media that are not available anywhere for sale and have less than 10 seeds, so I feel like I am helping keep the shows and movies of my childhood alive.
They did have a server seized (physically) in 2015: https://lemmy.dbzer0.com/post/6754830
Though apparently there were no logs.Interestingly though, that forum post was now deleted from AirVPN site. Strange…
Hmm, TIL, thanks.
Good person. Much like I would like to do. I’d be happy with a VPN for personal use and another one for torrenting (gluetun compatible preferably) Shall look at AirVPN, thanks.
Just switched to Mullvad and haven’t tried torrenting with it yet… Doesn’t work? Or just slow?
yes, but you can only download from peers with port forwarding enabled, and you can also only upload to port forwarding peers, so generally its fine for downloading, but if you want to keep ratio (uploading) on a private tracker you need port forwarding
I mean, if you set up your os on an encrypted ram disk, then set it to restart when the server rack door was unlocked/opened and didn’t leave a backdoor for yourself to remote in, you could have a situation where you entirely lack the capability to give them access to anything before that moment. A skilled hacker might be able to get in through an exploit or do something crazy with cryogenics to read the memory at the time of shutdown, but a quick restart would overwrite most of what’s in memory and scrub that
Legally, there’s not much better defense than “I’m sorry your honor, I can’t provide access to the running system in the same way I can’t un-shatter a smashed mug”. If someone shows up with a warrant, you could explain that it’ll wipe itself if they open or unplug it, and it might’ve done so already. Then you guide them to it, hand over the key to the server cabinet, and let them decide to open the cabinet and destroy evidence so they can take it with them. Or they can take you at your word, and give up.
Court orders can’t break physics, and as a VPN your reasoning for setting up the system like this is to make your service more appealing to customers - the purpose is not to aid in a crime or destroy evidence, it’s just the normal course of business.
The same way that most companies wipe their emails after 30 days - yes, it potentially destroys incriminating paper trails, but that’s just a side effect of the security policy you’ve had all along
Granted, there’s probably some sketchy sealed laws they could use to force you to backdoor your own system moving forward, but you can fight that as it’s undue hardship. It requires a non-negligible amount of work and would make your product less competitive
They might win in the end if they keep pushing, and even might be able to order you to “keep up the canary paper” (meaning keep claiming not even you have access to the running system), but more likely they’d get a warrant for your customer financial records and try to find an easier path to find what they want elsewhere
You really dont need to do all that if you just dont log to begin with
True, it’s probably overkill. But even if you don’t log, they could theoretically start live monitoring the VPN with a court order… With a setup like this, there’s no front door or backdoor, just an ephemeral image you have to restart to modify. You’d have to write in access methods and rebuild to get in… The government can’t just walk in and demand you stop what you’re doing and build something for them
It does add security, even if you might not need that level of security
And here I thought companies can’t go to jail. Apparently that only applies to the companies who aren’t run by the lizard people or the kids popular with the priests.
The only reason I look at IVPN is because they allow port forwarding
They no longer offer this, right?
They don’t?
deleted by creator
Unfortunate. I like their model
Try AirVPN. They allow port forwarding and have fairly extensive configuration options.
I like AirVPN, my main issue is server stability. iVPN and Mullvad at least were able to maintain a connection continuously for weeks on end across various networks, but this is not the case for AirVPN. It’s to the point where I’m considering alternatives because I’ll start using my device only to find out the VPN tunnel has died and I have to manually reconnect it.
Been using them for many years and several instances I leave permanently connected. I can’t recall a single instance of AirVPN disconnecting from their side.
This has been killing me too. Refuses to stay connected and I haven’t figured out how to run kdeconnect (worked fine with mullvad’s cli command lan set allow, doesn’t work with airvpn’s “allow lan” toggle.)
Soooo how to split the packets up between 3 VPNs to make each providers piece useless?
You’re about 15% of the way to re-inventing Tor.
check out Nym, they are doing this kind of network
Sounds very similar to Safing Privacy Network. They route different applications across nodes (Tor-esque).
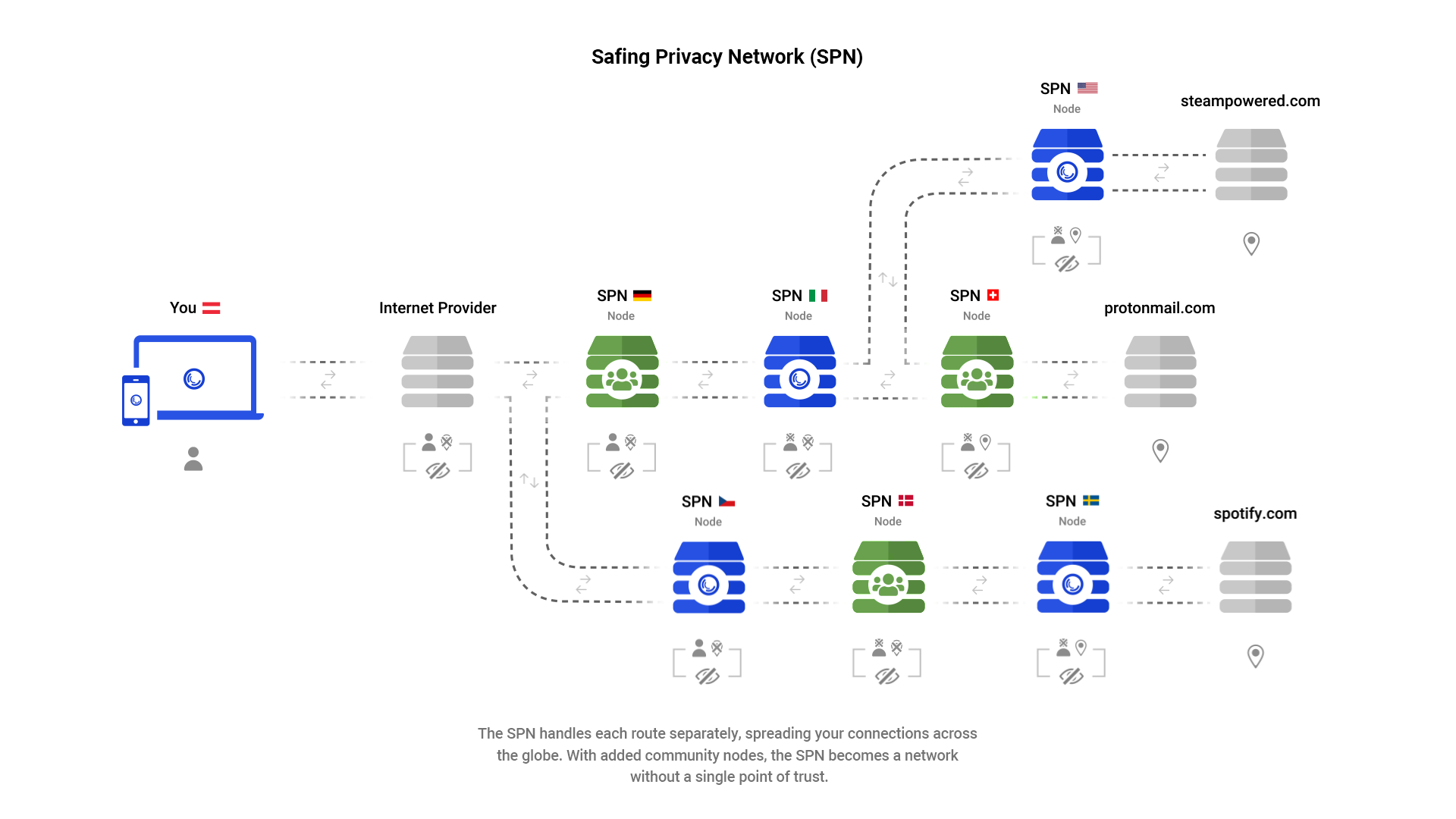
That does not work unless you involve yet another party after the VPNs and before the destination to rebuild the packets, as the destination won’t know what to do with these split packets.
At that point you may be better off using an anonymity network with or without the VPN.
I’ve tried IVPN a number of times but it never works for getting around mlb.tv blackouts which is my biggest use case. ExpressVPN has just been reliable for me in that regard.
IVPN servers are all well-known and catalogued. ExpressVPN partly buys hacked machines to user as proxies for their paid tier user VPNs, so they are much less likely to be blocked. They have a lot more… troubling history, that would make me never visit their download site.
Kape Technologies has announced plans to acquire ExpressVPN for $986 million. I do have concerns about this because Kape was once considered a malware provider.
Reuters indicating that ExpressVPN CIO Daniel Gericke is among three men fined $1.6 million by the US Department of Justice for hacking and spying on US citizens on behalf of the government of the UAE (United Arab Emirates).
Kape Technologies has had quite a convoluted history. According to a report in Forbes, a company called Crossrider was formed in 2011 by “billionaire Teddy Sagi, a serial entrepreneur and ex-con who was jailed for insider trading in the 1990s. His biggest money maker to date is gambling software developer Playtech,” and Koby Menachemi.
Menachemi was a developer for Unit 8200, an Israeli signals intelligence unit responsible for hacking and collecting data (think of it as part CIA, part NSA, and part high school, because the unit hires and trains teenagers in hacking and coding skills).
the newly renamed Kape Technologies set out on an acquisition binge. The company started buying in 2017, acquiring CyberGhost VPN for about $9 million. Next, in 2018, came Mac antivirus company Intego for $16 million. A few months later, Kape gobbled up another VPN provider, ZenMate, for about $5 million. A year later, in 2019, Kape spent $95 million for Private Internet Access, one of the best known VPN providers at the time.
There’s more to the story as well, but you can be sure that all your data is
belongeither being proxied by a botnet, or being used to spy on you. ‘I have nothing to hide!’ you may say, but I’m sure you have an app or two that still uses insecure HTTP update checks, which can be intercepted to trigger a malware installation.Appreciate the info. Do you have any recommendations for alternatives? I do see reports that NordVPN seems to work for mlb blackouts but nothing on mullvad, however I could trial them I suppose.
Edit: tried mullvad and mlb.tv won’t even allow the login 😞
You’ll want a provider with a ton of servers. For bypassing service level blocks, either a VPN like Express with thousands of servers or your own VPN is the way to go. there are docker images for setting up a VPN on a $5 VPS.
it depends on your risk tolerance. do you need to stay as anonymous as possible (with VPN as layer 1) or do you need to be able to watch shows in a different language? Mullvad and IVPN have a limited set of rented and owned servers that are setup for security and privacy. Express, Nord, and those less ethical VPNs don’t care about that, they just want as many cheap servers as they can possibly get.
I personally think VPNs are mostly a waste of money
For “privacy” yes, almost entirely.
If your VPN isn’t routing to your home network so you can safely access selfhosted applications then you’re basically just sharing your traffic with a total stranger and trusting them not to run telemetry etc.
It depends who you trust more, your isp or your vpn provider. Isps are not known for doing right by their clients
You also have to trust your vpns isp.
you dont really. you share your connection with a bunch of other people, and if you then add multi hop that makes it exponentially harder for the VPN’s ISPs to somehow target you. Learn how VPNs work bro
I know how VPNs work. When I connect to a VPN I trust that the provider doesn’t snoop on me, actually routes the traffic like they promise and combines my traffic effectively enough that it obfuscates my identity.
correct, and, I trust that provider, i.e. Mullvad, 100x more than I trust my ISP. Especially after Mullvad’s run-in with the police last year. Recommend to look it up. Also OVPN’s court battle, and Proton’s court battles too. A good provider will prove themselves to you.
My point is that I disagree that a VPN provider is somehow intrinsically on the same trust level as an ISP. It really depends on the provider, but all in all VPN providers tend to be much more trustworthy with your traffic.
The VPN’s ISP will have a harder time to find out which part of the traffic belongs to a specific household.